What is TLS 1.0 & TLS 1.1
TLS 1.0 was released in 1999 as an improvement from SSL 2.0 and 3.0 as it resolved many vulnerabilities in those protocols. TLS 1.1 then arrived in 2006 with further security improvements. TLS 1.2 was released in 2008 and is the current standard along with the more recent TLS 1.3 released in August 2018 and both contain major security enhancements from the older version.
Why should I disable TLS 1.0 & TLS 1.1
The TLS 1.0 & TLS 1.1were formally deprecated as part of RFC 8996 in March 2021 after Apple, Google, Microsoft, and Mozilla jointly announced they would deprecate TLS 1.0 and 1.1 in March 2020. They were deprecated due to several security issues. All modern standards including the Mozilla Intermediate or Mozilla Modern standards that we test against during our web app pen testing, network pen testing, and mobile application pen testing services all state that TLS 1.0 and TLS 1.1 should be removed where possible.
Disabling TLS 1.0 & TLS 1.1 in Apache
Modify the configuration file that contains the SSLProtocol directive for your website. The location of this file may vary based on your platform, version, or installation specifics. Potential locations include:
- /usr/local/apache2/conf/extra/httpd-ssl.conf (default Apache installation)
- /etc/apache2/mods-enabled/ssl.conf (Ubuntu/Debian)
- /private/etc/apache2/extra/httpd-ssl.conf (macOS)
Once you’ve identified the appropriate configuration file, search for a line starting with SSLProtocol. In this illustration, derived from a default macOS Apache setup, SSLv3 is disabled using the – operator, but TLS 1.0 and 1.1 are enabled:
SSLProtocol all -SSLv3
To disable all outdated versions of SSL/TLS supported by Apache, specify them as follows:
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
The above configuration enables TLS 1.2, and if available in your environment, TLS 1.3 as well.
Disabling TLS 1.0 & TLS 1.1 in nginx
Specify SSL/TLS protocol settings in the primary Nginx configuration file, usually located at /etc/nginx/nginx.conf, or in your site configuration files. Look for a line beginning with ssl_protocols. For instance, the following is extracted from the default nginx.conf file of a fresh Nginx installation on Ubuntu:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3; # Dropping SSLv3, ref: POODLE
Edit this line to include only current, secure versions of SSL/TLS:
ssl_protocols TLSv1.2 TLSv1.3;
Keep in mind that settings in your default SSL configuration may be overridden by server blocks configuring individual domain names. Therefore, check for those if changes to your protocol settings are not reflected on your website.
After making configuration changes, reload Nginx to apply them. For more information, refer to Nginx’s documentation on configuring HTTPS servers.
Disabling TLS 1.0 & TLS 1.1 in IIS
Open RegEdit on the server or device and navigate to the following location: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols.
Add the and TLS 1.2 keys under Protocols: Right-click Protocols > Select New > Key > Name the key TLS 1.2. Create two keys Client and Server under TLS keys. Create the DWORD (32-bit) values under Server and Client key as follows: DisabledByDefault [Value = 0] and Enabled [Value = 1]
Disable TLS 1.0: Open regedit on the sever and navigate to the following location: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols.
Now change DWORD values under Server and Client under TLS 1.0: DisabledByDefault [Value = 0] and Enabled [Value = 0].
If TLS 1.0 entry does not exist in the registry, you can create a new key called TLS 1.0 and disable it.
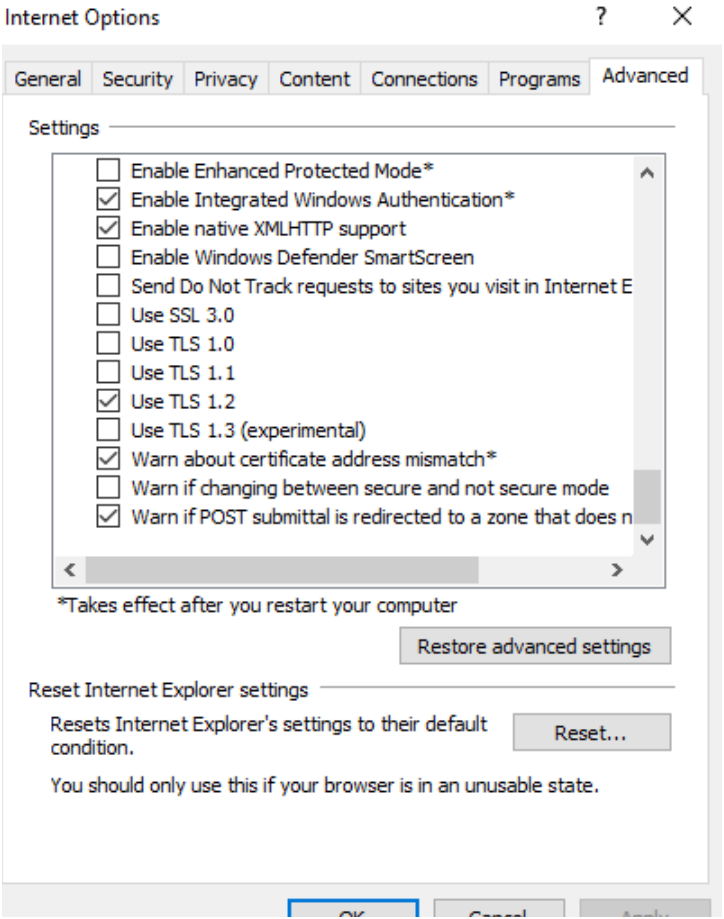
Verify that your server now supports TLS 1.2 protocol by following the below steps: Click the Windows button on the lower left-hand corner of your Desktop. Type “Internet Options” and select Internet Options from the list. Click on the Advanced tab and from there scroll down to the very bottom. Confirm that TLS 1.2 is checked. If it is not, please check the box adjacent to Use TLS 1.2 and then Apply.